Creating a Credential Store
- Click Add on the Credential Stores page. The Add New Credential Store dialog appears.
- From the Type drop-down, select which secure store is used. The available options depend upon which plugins have been enabled.
- The next steps will vary if you are creating an Orchestrator Database, CyberArk, or Azure Key Vault credential store.
Note:
You can only have one Orchestrator Database store.
Orchestrator Database
- Click Create, Orchestrator database stores do not have any configurable properties.
CyberArk
Note:
A CyberArk store configured in multiple tenants using the same App ID, Safe, and Folder Name, will permit access to stored credentials across tenants. To maintain tenant-level security and isolation, ensure different configurations are used for each tenant's CyberArk store.
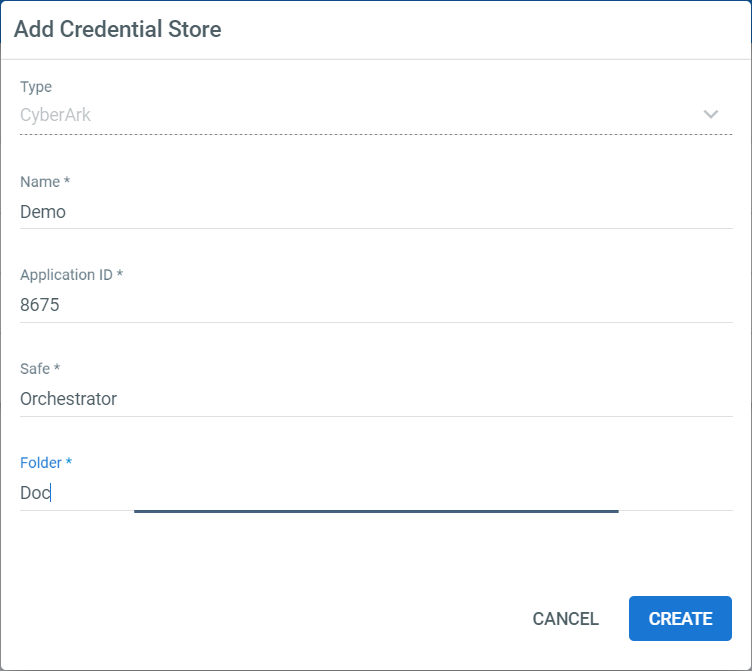
- In the Name field, type a name for the new credential store.
- In the App ID field, enter the application ID for your Orchestrator instance from the CyberArk® PVWA (Password Vault Web Access) interface. See here for details.
- In the CyberArk Safe field, enter the safe name as defined in the CyberArk® PVWA. See here for details.
- In the CyberArk Folder field, enter the location in which CyberArk® stores your credentials.
- Click Create. Your new credential store is ready for use.
CyberArk CCP
Note:
A CyberArk store configured in multiple tenants using the same App ID, Safe, and Folder Name, will permit access to stored credentials across tenants. To maintain tenant-level security and isolation, ensure different configurations are used for each tenant's CyberArk store.
- In the Name field, type a name for the new credential store.
- In the App ID field, enter the application ID for your Orchestrator instance from the CyberArk® PVWA (Password Vault Web Access) interface. See here for details.
- In the CyberArk Safe field, enter the safe name defined in the CyberArk® PVWA. See here for details.
- In the CyberArk Folder field, enter the location in which CyberArk® stores your credentials.
- In the Central Credential Provider URL field, enter the Central Credential Provider's address.
- In the Client Certificate field, upload the .pfx certificate to authenticate the requesting application against CCP. It can be either a self-signed certificate or a certificate signed by a Certificate Authority (CA). Import the client certificate or the root certificate authority used to sign it to the Trusted Root Certification Authorities certificate store on the CCP machine.
- In the Client Certificate Password field, enter the password of the client certificate.
- Optionally, in the Server Root Certificate field, upload a .crt certificate to provide data integrity for communication between the server and the client, in case the CCP vault is using a self-signed certificate
- Click Create. Your new credential store is ready for use.
Azure Key Vault
Key Vault credential stores use RBAC type authentication. After you've created a service principal, perform these steps:
- In the Name field, type a name for the new credential store.
- In the Key Vault Uri field, enter the address of your Azure Key Vault. This is
https://<vault_name>.vault.azure.net/. - In the Directory ID field, enter the directory ID found in the Azure portal.
- In the Client Id field, enter the Application ID from your Azure AD App Registrations section where the Orchestrator app was registered.
- In the Client Secret field, enter the secret needed to authenticate the client account entered in the previous step.
- Click Create. Your new credential store is ready for use.
Editing a Credential Store
Navigate to Credential Stores (Tenant > Credential Stores) and from the More Actions menu of the desired store, select Edit. The Edit Credential Store dialog appears is displayed.
Note:
The Orchestrator Database store does not have any editable properties.
Setting a Default Credential Store
When using 2 or more credential stores, you have the ability to select which is the default store used for Robots and Assets. The same store may be used as the default for both, or you can select a different default store for each.
To select a default store, from the More Actions menu, select Set as robots default store and/or Set as assets default store.
Deleting a Credential Store
To delete a credential store, select Remove from the More Actions menu of the desired store.
If the selected store is in use, a warning dialog will appear listing the number of robots and assets that will be affected. Click Delete to confirm the removal or Cancel to abort. Note that you must have at least one credential store active at all times. If only one is present, then the option to delete it does not appear.
Note:
A credential store designated as default cannot be deleted. You must first select a different default store for the credential type.
Updated about a year ago