Before you can begin to use CyberArk® credential stores in Orchestrator, you must first setup the corresponding application and safe settings in the CyberArk® PVWA (Password Vault Web Access) interface.
Prerequisites
- The CyberArk® plugin is set in your Orchestrator
web.configfile as described here. - CyberArk® Enterprise Password Vault must be installed on a machine that can communicate directly with the one where Orchestrator is installed.
- CyberArk® AAM (Application Access Manager) must be installed on the same machine as Orchestrator. For multi-node Orchestrator configurations, an AAM instance must be installed on each Orchestrator node.
Note:
If upgrading an Orchestrator instance with an existing CyberArk® configuration in the
web.configfile, a credential storeCyberArk Robot Credentialswith those settings will be automatically created in all tenants and set as the default store for robots. Your existing robots are migrated to this new credential store.
For more information about installing and configuring CyberArk® applications, please visit their official page.
Configuring the Integration
From the CyberArk® PVWA, you must perform the following steps:
- Create an application for your Orchestrator instance and add allowed machines;
- Create a Safe and add members to it to ensure proper permissions.
Creating an Orchestrator Application
- In CyberArk®’s PVWA, log in with a user that has permissions to manage applications (it requires Manage Users authorization).
- In the Applications tab, click Add Application. The Add Application page is displayed.
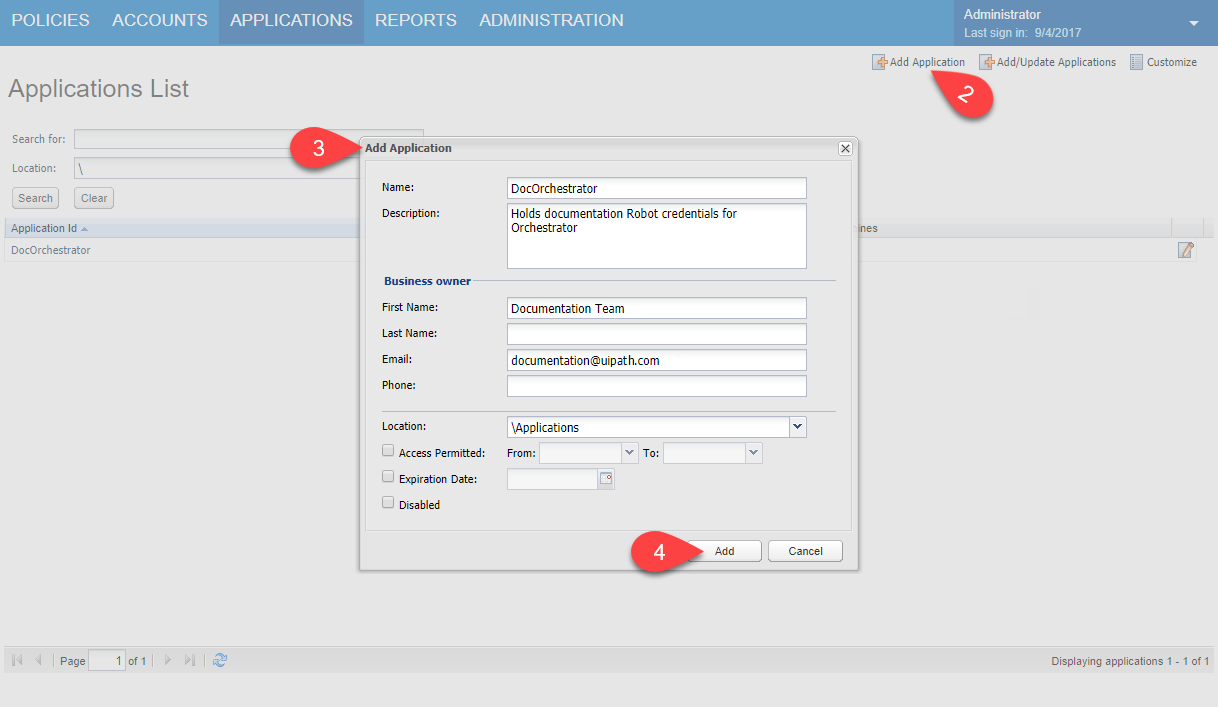
- Specify the following information:
- Name field - a custom name for the application, such as Orchestrator.
- Description - a short description to help you specify the purpose of the new application.
- Business owner section - optionally, add information about the application's Business owner.
- Location - the path of the application within the Vault hierarchy. If a Location is not specified, the application is added in the same Location as the user who is creating this application.
- Click Add. The application is added and its details are displayed in the Application Details page.
- In the Authentication tab, select the Allow extended authentication restrictions check box.
- In the Allowed Machines tab, click Add. The Add allowed machine window is displayed. Here you should add information about the machine or machines on which Orchestrator is installed.
- In the Address field, specify the address of a machine using the
IP/hostname/DNSformat. - Click Add. The IP address is listed in the Allowed machines tab. This information enables the Credential Provider to make sure that only applications that run on the specified machines can access their passwords.
- Perform steps 6 - 8 as many times as needed to ensure that the servers allowed include all mid-tier servers or all endpoints where the AAM Credential Providers were installed. This might be the case if you installed Orchestrator on multiple nodes.
Creating an Orchestrator Safe
Safes are required to help you better manage your accounts. Also, you can add safe members to ensure a proper authorization. CyberArk® recommends adding a credential provider (a user that has full rights over the credentials, can add and manage them) and the previously created application as safe members. The latter enables Orchestrator to find and retrieve the passwords stored in the safe.
- In the Policies tab, under the Access Control (Safe) section, click Add Safe. The Add Safe page is displayed.
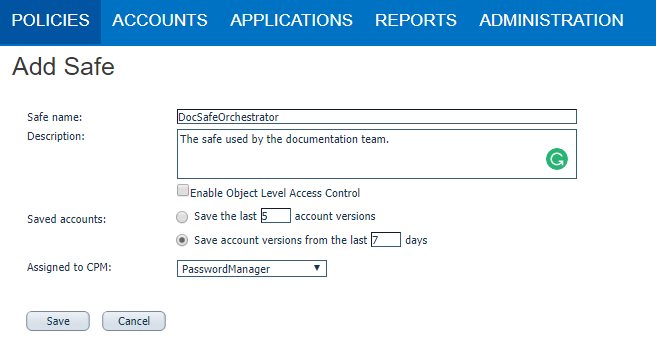
- Fill in the Safe Name field and Description fields.
- Click Save. The Safe Details window is displayed.
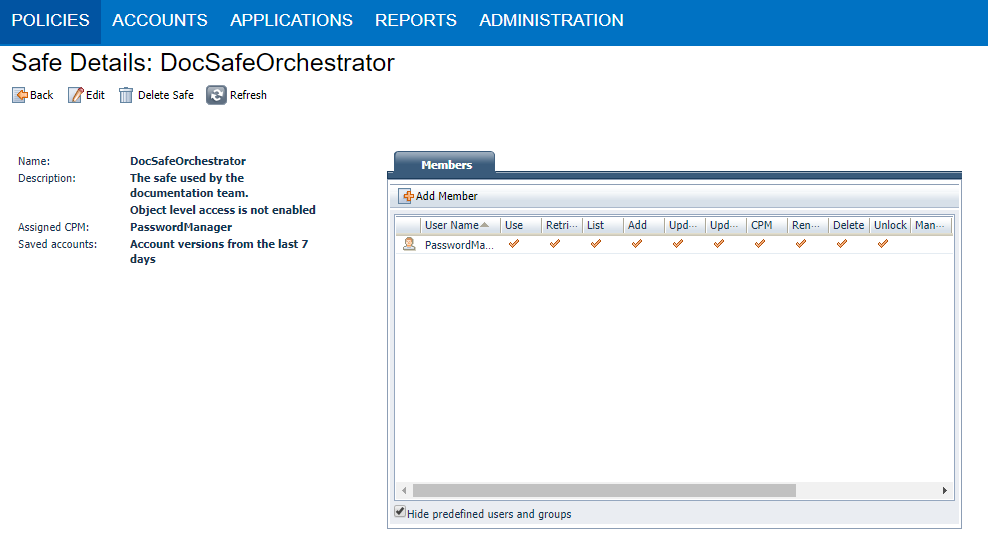
- In the Members section, click Add Member. The Add Safe Member window is displayed.
- Search for the previously created application (steps 2-5) so you can add it.
- Add a credential provider, and select the following permissions for it:
- View Safe Members
- Retrieve accounts
- List accounts
- Access Safe without Confirmation - Only if you are using a dual control environment and a v7.2 or lower PIM-PSM.
If you install multiple credential providers for this integration, it is recommended to create a group for them, and add the group to the Safe once with the above authorization.
- Click Add. A confirmation message is displayed in the Add Safe Member window.
- Add the previously created application as a safe member, with the Retrieve accounts permission.
- Click Add. A confirmation message is displayed in the Add Safe Member window.
Your integration is complete and you can begin provisioning CyberArk® credential stores in Orchestrator. For details on storing Robot credentials, see here.
Updated 2 years ago