Configure OKTA to Recognize a New Orchestrator Instance
Note:
The below steps are valid for OKTA SAML setup. Please note that the below procedure is a broad description of a sample configuration. For a fully detailed how-to, visit the official OKTA Documentation.
- Login to OKTA. The following setup is made in Classic UI view. You can change it from the drop-down on the top-right corner of the window.
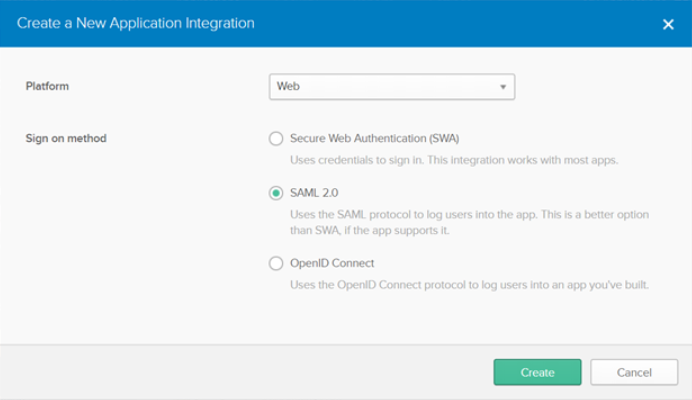
- On the Application tab, click Create New App. The Create a New Application Integration window is displayed.
- Choose SAML 2.0 as sign-on method and click Create.
- For the new integration, on the General Settings window, enter the application name.
- On the SAML Settings window, fill in the General section as per this example:
- Single sign on URL: The Orchestrator instance URL +
/Saml2/Acs. For example,https://platform.uipath.com/Saml2/Acs. - Enable the Use this for Recipient URL and Destination URL check box.
- Audience URI:
https://platform.uipath.com - Name ID Format: EmailAddress
- Application Username: Email
- Single sign on URL: The Orchestrator instance URL +
Note
Whenever filling in the URL of the Orchestrator instance, make sure it does not contain a trailing slash. Always fill it in as
https://platform.uipath.com, nothttps://platform.uipath.com/.
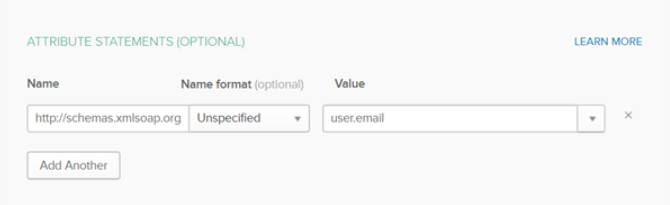
- Click Show Advanced Settings and fill in the Attribute Statements section:
- Set the Name field to
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddressand select user.email from the Value drop-down.
- Set the Name field to
- Download the OKTA certificate.
- In the Feedback section, select the option that suits you and click Finish.
- On the Sign On tab, in the Settings section, click Setup Instructions. You are redirected to a new page containing the instructions required to complete your Orchestrator configuration for SAML 2.0: Identity Provider Sign-On URL, Identity Provider Issuer, X.509 Certificate.
Note
If, for any reason, the information about the identity provider is lost, you can, at any point, visit Sign On > Settings > View Setup Instructions.
Assigning People to the Application
In order for a user to be able to use OKTA authentication, he must be assigned the newly created application:
- Login to OKTA.
- On the Application page, select the newly created application.
- On the Assignments tab, select Assign > Assign to People and then select the users to be given the necessary permissions.
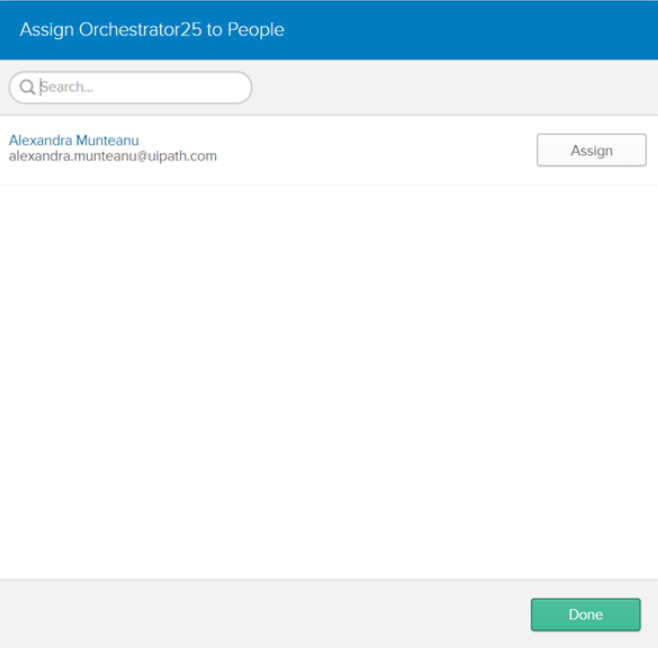
- The newly added users are displayed on the People tab.
Set Orchestrator to Use OKTA Authentication
- Define a user in Orchestrator and have a valid email address set on the Users page.
- Import the signing certificate provided by the Identity Provider to the Windows certificate store using Microsoft Management Console. See step 9 in the Configure OKTA to Recognize a New Orchestrator Instance procedure.
- Make sure that the following configuration is present in
web.config:
<configuration>
<appSettings>
<add key="ExternalAuth.Saml2.Enabled" value="true" />
</appSettings>
<sustainsys.saml2 entityId="https://platform.uipath.com" returnUrl="https://platform.uipath.com/Account/ExternalLoginCallback">
<identityProviders>
<add entityId="http://www.okta.com/exkh2ti6zlefzZPT50h7" signOnUrl="https://dev-786854.oktapreview.com/app/uipathdev786854_orchestrator26_1/exkh2ti6zlefzZPT50h7/sso/saml" allowUnsolicitedAuthnResponse="true" binding="HttpRedirect">
<signingCertificate storeName="My" storeLocation="LocalMachine" x509FindType="FindByThumbprint" findValue="30c4de7f241904544ca663689146769c914c5dd2"/>
</add>
</identityProviders>
</sustainsys.saml2>
</configuration>
- Replace all occurrences of
https://platform.uipath.comwith the URL of your Orchestrator instance. Make sure to add/Account/ExternalLoginCallback/at the end of the URL for thereturnUrlparameter. This path is specific to OKTA as it allows you to reach an Orchestrator environment directly from OKTA. For example,https://platform.uipath.com/Account/ExternalLoginCallback.
- Replace all occurrences of
- Set the
entityIdparameter to the value obtained by configuring OKTA authentication. See step 9 in the Configure OKTA to Recognize a New Orchestrator Instance procedure. - Set the
signOnUrlparameter to the value obtained by configuring OKTA authentication. See step 9 in the Configure OKTA to Recognize a New Orchestrator Instance procedure. - Set the
findValueattribute of thesigningCertificateparameter to the thumbprint of the certificate, as provided in the Windows certificate store. Details here.
Note
Whenever filling in the URL of the Orchestrator instance, make sure it does not contain a trailing slash. Always fill it in as
https://platform.uipath.com, nothttps://platform.uipath.com/.
Updated 2 years ago