Important!
Logging in to Orchestrator using the Internet Explorer or Edge web browsers does not work if the name of your website contains an underscore (“_”), such as
https://orchestrator_tests.com.
You can log in to Orchestrator with:
- A user account previously created in the Users page (For more information, see the Managing Users page). Please note that on the first login, these users have to reset their password.
- A user account under a Windows Active Directory group that was previously added in the Users page. For more information, see Adding Directory User. By default, the [NTLM authentication protocol][1] is used. To switch to [Kerberos][2], please take a look at this page.
[1]: https://docs.microsoft.com/en-us/previous-versions/msp-n-p/ff647076(v=pandp.10)#ntlm-authentication
[2]: https://docs.microsoft.com/en-us/previous-versions/msp-n-p/ff647076(v=pandp.10)#kerberos-authentication - A user account under a Microsoft Azure Active Directory group that was previously added in the Users page. For more information, see Adding Directory User and these
web.configsettings).
Logging in with the same user on a different machine or browser session disconnects the user from the first machine/session.
If external users (from the Windows or Azure AD) are members of multiple tenants, when they log in they are redirected to the Choose Tenant page.
Note:
It is not recommended to use Microsoft Azure AD and Windows AD on the same Orchestrator instance.
You can also set up your environment to automatically log in to Orchestrator, on the default tenant.
If you enable AutoLogin and access an Orchestrator URL without being authenticated the app tries to automatically log in with your current Active Directory user, without redirecting to Login page. If AutoLogin is disabled you are redirected to Login page and have to manually press the "Windows" button to perform a Windows Login.
Logging in with an Orchestrator User Account
Note:
The user must first be created in the Users page.
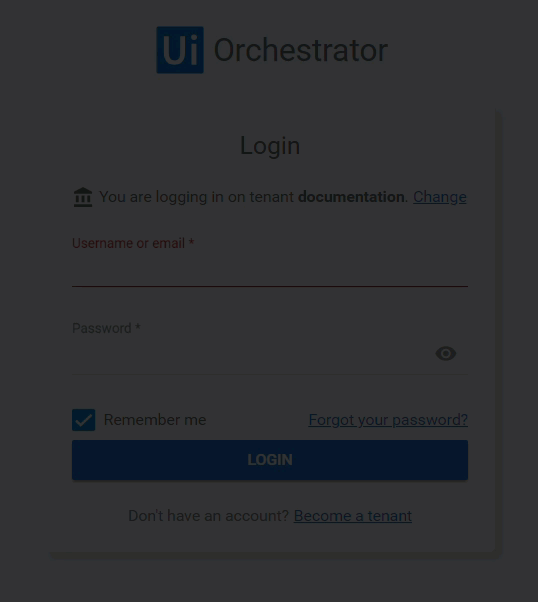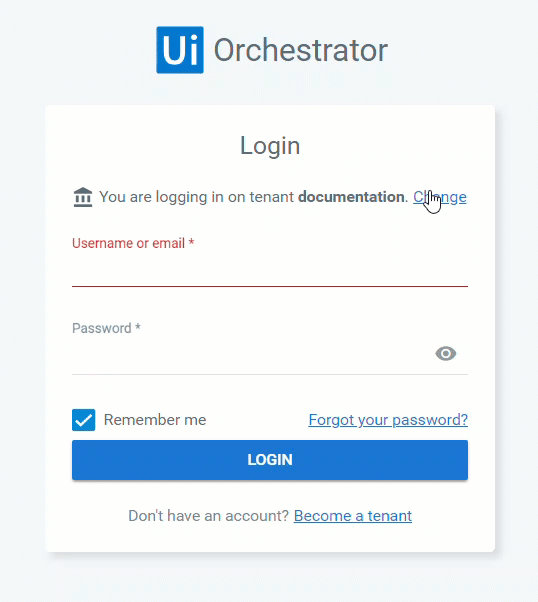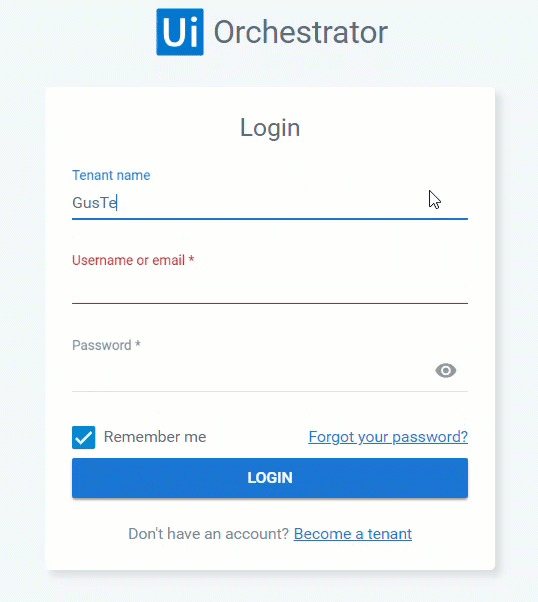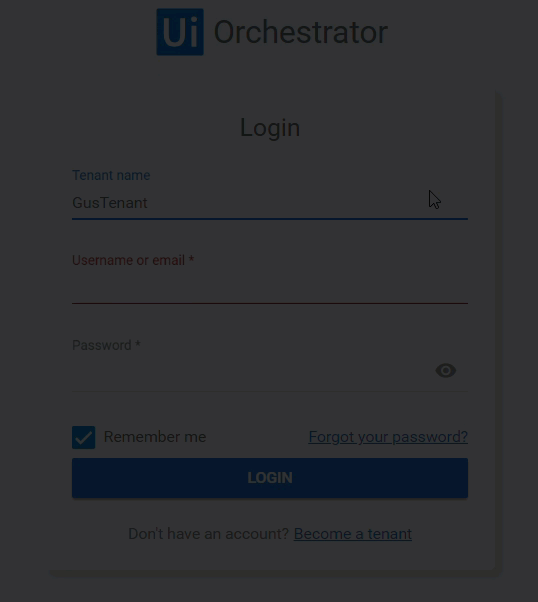
- Fill in the Tenant name field. The last tenant used for authentication is remembered so if you want to use a different one, first click Change and then fill in the name.
-
Fill in the Username or email and Password fields.
-
(Optionally) Select the Remember me check box. This enables you to automatically login later on.
-
Click Login. The first time you log in, the Change Password page is displayed in order for you to define a new password.
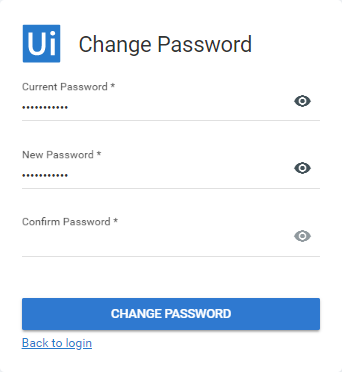
- In the Current Password field, type the password that was given to you by your Orchestrator administrator.
- In the New Password and Confirm Password fields, type a password of your choice.
- Click Change Password. Your password is changed, and Orchestrator is loaded. Access is provided to components according to the assigned role(s) and organization unit (if any).
After 10 failed login attempts the user is locked out for 5 minutes. These are the default Account Lockout settings which can be changed in the Security tab.
Logging in with a User from an Active Directory Group
Important!
This login method is only available for Orchestrator with Enabled Windows Authentication.
The Active Directory user or group must first be added in the Users page.
- Click either the Windows or Azure button from the Orchestrator login screen.
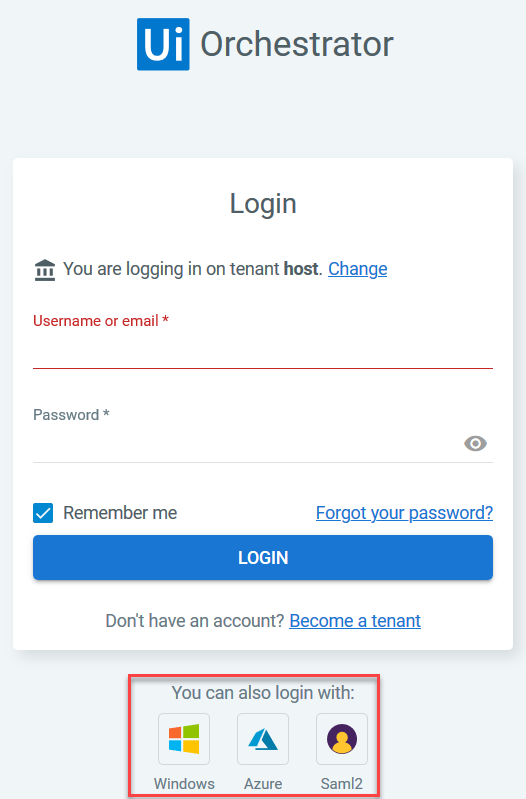
- You are logged in automatically and the Orchestrator dashboard is displayed. If the AD user or group has not been added to Orchestrator, the Authorization Required dialog appears.
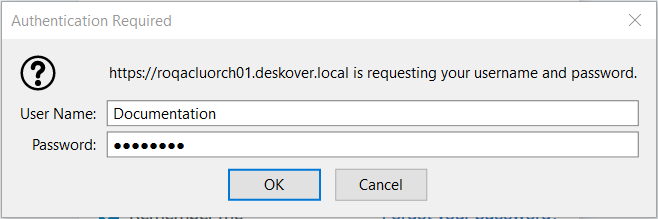
- Fill in the User Name and Password fields.
- Click Log In. Orchestrator is loaded and access is provided to components according to the assigned role(s).
Note:
By default, the user is locked for 5 minutes after 10 failed login attempts. You can change this in the Settings window under the Security tab.
Updated 2 days ago